Forensics
Beginner to Mastery
Certified Forensics Analyst
Comprehensive training in digital forensics and cyber investigations.
Hands-on projects simulating real-world cybercrime scenarios.
Practical exposure to evidence collection, memory analysis, and OS forensics.
Curriculum aligned with latest tools, techniques, and legal frameworks.

Course Duration
300 Hours
Next Batch
23 November 2025
Course Material
Live. Online. Interactive.
Expert guidance and mentorship for building industry-ready skills.

KEY HIGHLIGHTS OF CERTIFIED FORENSICS ANALYST PROGRAM
- Weekly sessions with industry professionals
- Dedicated Learning Management Team
- 300 hours of hands-on learning experience
- Over 90 hours live sessions spread across 04 months
- 90 hours of self-paced Learning
- Learn from Industry Experts.
- More than 10+ industry-related projects and case studies
- One-on-One with Industry Mentors
- 24*7 Support
- Dedicated Learning Management Team
- 1:1 Mock Interview
- No-Cost EMI Option
- Designed for both working professionals and fresh graduates
- High Demand and Career Opportunities
- Competitive Edge and Innovation
- Problem-Solving and Critical Thinking
WHY JOIN CERTIFIED FORENSICS ANALYST PROGRAM?
Comprehensive Learning
Gain knowledge of digital forensics, covering evidence collection, system forensics, incident response, and legal aspects.
Hands-On Learning
Engage in practical labs and real-world case studies to apply your learning.
Industry-Relevant Tools
Work with tools like FTK Imager, Volatility, and Cyber Triage, used by professionals in forensics.
Expert Guidance
Learn from instructors with experience in digital forensics, cybersecurity, and incident response.
UPCOMING BATCH:
23 November 2025

SkillzRevo Solutions
30 MINUTE MEETING
Web conferencing details provided upon confirmation.
Corporate Training, Enterprise training for teams
Batch schedule
| Batch | Batch Type |
|---|---|
| Online Live Instructor Led Session | Full-Time |
| Online Live Instructor Led Session | Part-Time |
Regional Timings
| Batch | Batch Type |
|---|---|
| IST (India Standard Time) | 09:00 PM–12:00 AM |
| Bahrain, Qatar, Kuwait, Saudi Arabia | 06:30 PM–09:30 PM |
| UAE / Oman | 07:30 PM–09:00 PM |
Certified Forensics Analyst OVERVIEW
This digital forensic program offers a broader and hand learning experience, which equip the participants with the skills and knowledge required to identify, investigate and react to cyber crime and safety events. Along with focusing on various aspects of digital forensic, including evidence collection, system and OS forensic, memory analysis and event reaction-this course provides intensive coverage of equipment, techniques and legal ideas involved in the forensic investigation. Students will get practical experience through attractive projects, which will help them to create proficiency for real -world application.
ENROLL NOW & BOOK YOUR SEAT AT FLAT 50% WAIVER ON FEE
Enroll Now →Certified Forensics Analyst Objectives
This course is to equip participants with a comprehensive understanding of Digital Forensics, from Foundational Principles to Advanced Investigative Techniques. By the end of the program, Learners will be Proficient in Collecting, Preserving, and Analyzing Digital Evidence from Various Platforms, Including Computers, Mobile Devices, Mobile Devices, Mobile Devices, and Cloud Env. They will also get expertise in the event response, malware analysis and memory forensic using industry-standard equipment. Additionally, the course aims to develop participants' ability to conduct thorough Forensic Investigations, Prepare Detailed Reports, and Navigate the Legal and Regulatory Aspects of Digital Forensic, Their findings are admissible in court. Overall, the course is designed to Empower Learners to Tackle Real-world Cyber Security challenges and make meaningful contributions to the field of digital forensics.
Enroll Now →Why Learn Certified Forensics Analyst ?
Master Digital Forensics Principles
Understand core concepts such as evidence handling, forensic investigation lifecycle, and the methodologies applied in modern forensic practices.
Collect and Analyze Digital Evidence
Gain hands-on skills in acquiring and analyzing evidence from diverse systems including Windows, Linux, mobile, memory, and cloud environments.
Advance Incident Response Skills
Learn to conduct incident response and malware analysis, understand attack patterns, and apply effective recovery strategies.
Utilize Industry-Leading Tools
Master forensic tools and techniques to uncover hidden data, trace security breaches, and support legal investigations with accuracy.
Develop Professional Forensic Reporting
Build expertise in creating detailed, clear, and comprehensive forensic reports for both technical experts and non-technical stakeholders.
Gain Real-World Experience
Work on practical projects and case studies that simulate real cybercrime scenarios, preparing you for industry challenges.
Program Advantages
Practical labs and real-world case studies to apply your learning in a controlled environment.
Learn from seasoned professionals with extensive experience in digital forensics, cybersecurity, and incident response.
Gain hands-on experience with industry-standard tools like FTK Imager, Volatility, Cyber Triage, and more.
Explore a variety of topics such as evidence collection, Windows and Linux forensics, memory analysis, incident response, and cyber law.
Participate in hands-on projects to analyze cyber-attacks, perform malware analysis, and simulate corporate cyber incidents.
A mix of live sessions, recorded materials, and self-paced assignments offers flexible learning.
Understand legal frameworks in digital forensics, including data privacy regulations and the chain of custody.
Ensure compliance with global and regional laws regarding digital evidence handling.

Certified Forensics Analyst program Certifications
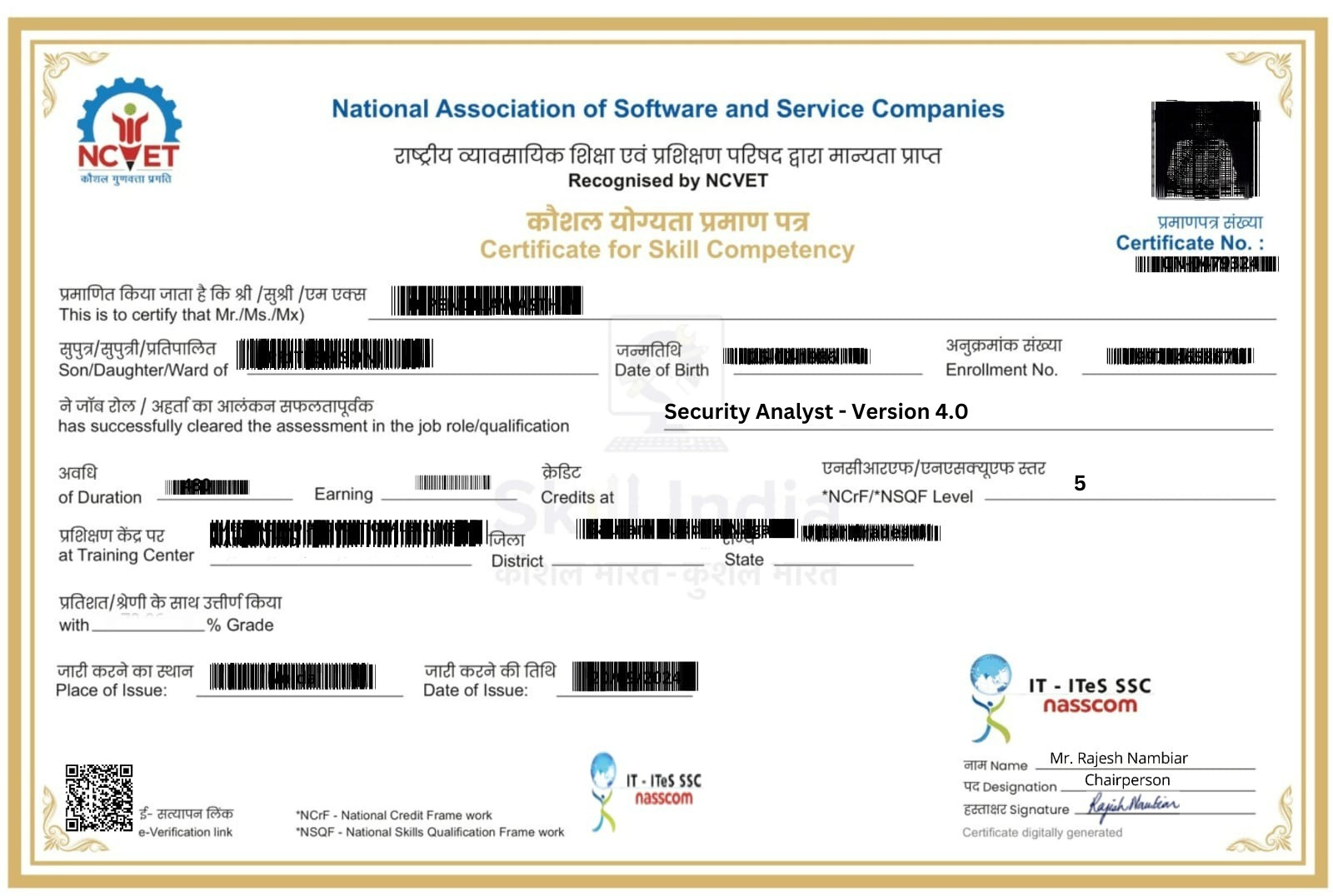
Nasscom

Course Completion

Project Completion
Certified Forensics Analyst Curriculum
Certified Forensics Analyst Skills Covered
Certified Forensics Analyst Tools Covered

Certified Forensics Analyst Program Benefits

CAREER OPPORTUNITIES AFTER THIS COURSE
Incident Response Specialist Salary Range
Min
$70,000
Average
$90,000
Max
$110,000

MASTER DIGITAL FORENSICS WITH REAL-WORLD PROJECTS
Work on Practical Case Studies
Guided by Industry Experts
Simulate Real Cybercrime Scenarios
Capstone Projects of this Program
Job Obligation After This Course
WE CAN APPLY FOR JOBS IN
Investigating cybercrimes and analyzing digital evidence to identify attack sources and gather forensic data.
Responding to security incidents, containing threats, and recovering compromised systems.
Monitoring network traffic and system logs, detecting potential threats, and preventing security breaches.
Performing ethical hacking to identify vulnerabilities and help organizations enhance their security measures.
Designing and implementing security systems such as firewalls and intrusion detection systems (IDS).
Recovering and securing data from compromised or damaged systems using forensic tools.
Managing security operations, continuously monitoring for threats, and ensuring the security of enterprise networks.
Advising organizations on best practices for protecting data, systems, and networks from cyber threats.
Companies Hiring for this Course
















































































































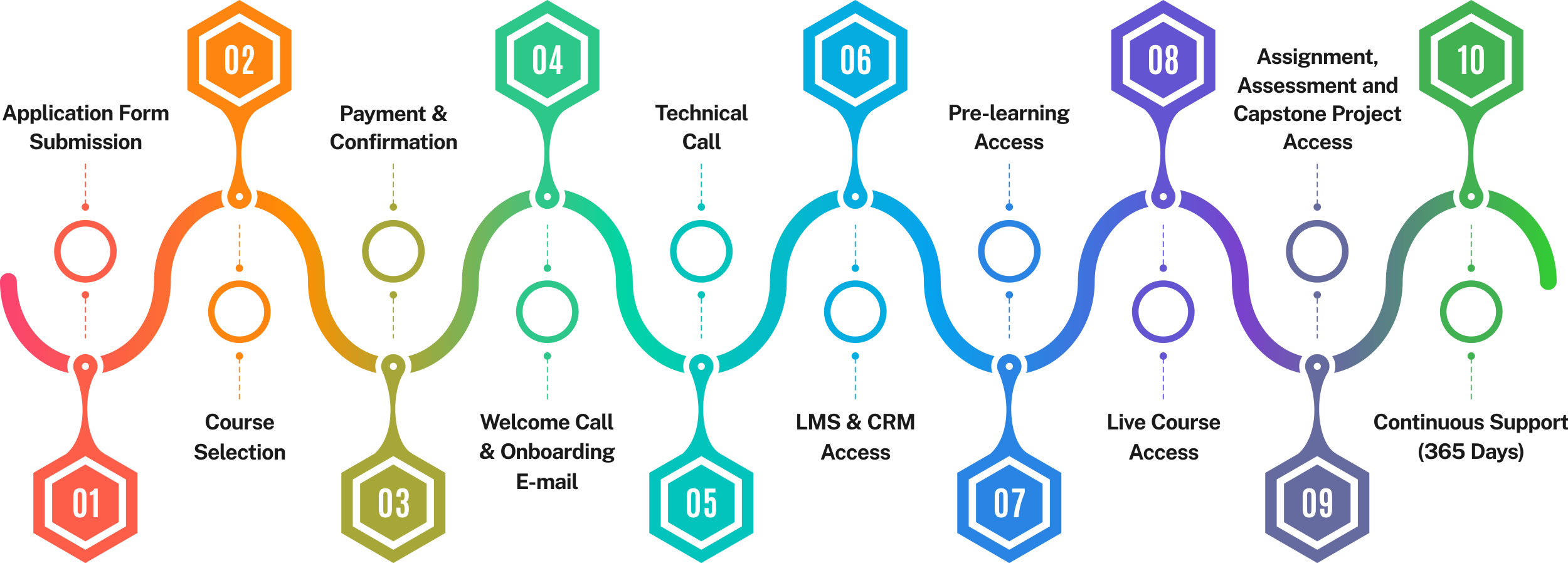
Admission Process
The application process consists of three simple steps. An offer of admission will be made to selected candidates based on the feedback from the interview panel. The selected candidates will be notified over email and phone, and they can block their seats through the payment of the admission fee.
Course Fees & Financing
We partnered with financing companies to provide competitive finance options at 0% interest rate with no hidden costs.


UPCOMING BATCHES/PROGRAM COHORTS
| Batch | Date | Time (IST) | Batch Type |
|---|---|---|---|
| Online Live Instructor Led Session | 23 November 2025 | 9 PM to 12 AM | Batch 1 |
| Online Live Instructor Led Session | 30 November 2025 | 9 PM to 12 AM | Batch 2 |
COMPARISON WITH OTHERS
| Feature | Our Course | COMPETITOR A | COMPETITOR B |
|---|---|---|---|
| Curriculum Scope | Comprehensive: Python, ML, DL, NLP, CV, Generative AI | Basic ML and DL focus | General AI with less focus on Generative AI |
| Hands-On Experience | Extensive practical projects with tools like GPT, DALL-E 2 | Limited practical projects | Hands-on projects mainly in traditional AI |
| Advanced Tools | GPT, DALL-E 2, Midjourney, Hugging Face, Transformers, GANs, RAG, LangChain | Focus on traditional ML frameworks | Emphasis on standard ML and AI tools |
| Instructor Expertise | Experienced professionals with industry and research background | Mix of industry and academic instructors | Primarily academic-focused instructors |
| Real-World Applications | Emphasis on real-world problem-solving and innovation | Mostly theoretical applications | General applications with less focus on innovation |
| Career Support | Strong focus on career advancement and networking | Basic career services | Limited career support and networking opportunities |
| Networking Opportunities | Connect with peers and industry leaders | Limited networking events | Few networking opportunities |
| Certification Value | Recognized certification for advanced AI roles | Standard certification | General certification with less industry recognition |