Cybersecurity
Beginner to Mastery
Certified Network Security and Ethical Hacking Specialist
Capstone Project Discussion & Doubt Clearing Session: 10 Hours
Learn from IIT Faculty & Industry experts
More than 40+ industry-related projects and case studies
Personalised mentorship sessions with industry experts

Course Duration
350 Hours
Next Batch
23 November 2025
Course Material
Live. Online. Interactive.
24*7 Support
Dedicated Learning Management Team
Designed for both working professionals and fresh graduates
High Demand and Career Opportunities

KEY HIGHLIGHTS OF CERTIFIED NETWORK SECURITY AND ETHICAL HACKING SPECIALIST PROGRAM
- Weekly sessions with industry professionals
- Dedicated Learning Management Team
- Duration of Course: 350 Hours
- 350 hours of hands-on learning experience
- Over 115 hours of live sessions spread across 5 months
- 115 Hours of Class Recording with Lifetime Access
- Pre-Learning Material: 70 Hours
- Total No of Weeks: 20
- Capstone Project Discussion & Doubt Clearing Session: 10 Hours
- Learn from IIT Faculty & Industry experts
- More than 40+ industry-related projects and case studies
- Personalised mentorship sessions with industry experts
- 24*7 Support
- Dedicated Learning Management Team
- 1:1 Mock Interview
- No-Cost EMI Option
- Designed for both working professionals and fresh graduates
- High Demand and Career Opportunities
- Competitive Edge and Innovation
- Problem-Solving and Critical Thinking
WHY JOIN CERTIFIED NETWORK SECURITY AND ETHICAL HACKING SPECIALIST PROGRAM?
Comprehensive Learning
Gain a broad understanding of essential data science and AI tools, from foundational skills to advanced techniques.
Real-World Application
Apply theoretical knowledge to practical projects, preparing you for real-world data challenges.
Cutting-Edge Skills
Stay ahead in the industry with training in the latest technologies like Generative AI and advanced Big Data tools.
Career Growth
Enhance your qualifications and open doors to high-demand roles in data science, AI, and Big Data.
UPCOMING BATCH:
23 November 2025

SkillzRevo Solutions
30 MINUTE MEETING
Web conferencing details provided upon confirmation.
Corporate Training, Enterprise training for teams
Batch schedule
| Batch | Batch Type |
|---|---|
| Online Live Instructor Led Session | Full-Time |
| Online Live Instructor Led Session | Part-Time |
Regional Timings
| Batch | Batch Type |
|---|---|
| IST (India Standard Time) | 09:00 PM–12:00 AM |
| Bahrain, Qatar, Kuwait, Saudi Arabia | 06:30 PM–09:30 PM |
| UAE / Oman | 07:30 PM–09:00 PM |
Certified Network Security and Ethical Hacking Specialist OVERVIEW
The Certified Network Security and Ethical Hacking Specialist (CNSEHS) program is a comprehensive training course that equip the participants with both theoretical knowledge and expertise in the theoretical knowledge and hands in network safety. Through practical laboratories, case studies and real -world simulations, the learner will achieve proficiency in using moral hacking techniques to secure and reduce the wreckers, to implement and reduce security principles and strengthen safety. With the emphasis on moral practices and adherence to global cyber security standards such as ISO framework and compliance rules, this program prepares individuals to develop cyber threats. Whether you are an ambitious cyber security professional or an IT specialist to pursue your career, this certification provides in-demand skills required for important roles in network security and moral hacking.
ENROLL NOW & BOOK YOUR SEAT AT FLAT 50% WAIVER ON FEE
Enroll Now →Certified Network Security and Ethical Hacking Specialist Objectives
The Certified Network Safety and Moral Hacking Experts (CNSEHS) program aims to equip participants with a deep understanding of cybersecurity, moral hacking, and network safety through a mixture of theoretical knowledge and hands-on experience. Learners will specialize in penetration testing, vulnerability evaluation, and advanced security measures to protect IT infrastructure from cyber threats. The course includes cryptographic theory, safety violation detection, risk mitigation, and compliance with global cybersecurity standards such as ISO and NIST. Additionally, participants will work with industry-standard equipment, engage in real-world projects, and develop practical skills required for the identification, analysis, and response to security events. By the end of the program, learners will be well prepared for important roles in cybersecurity and moral hacking, ensuring the safety of digital assets and defending against developing cyber threats.
Enroll Now →Why Learn Certified Network Security and Ethical Hacking Specialist ?
HIGH DEMAND FOR CYBERSECURITY PROFESSIONALS
With increasing cyber threats like phishing, ransomware, and DDoS attacks, organizations are actively seeking experts to safeguard their systems.
COMPREHENSIVE COVERAGE OF CYBERSECURITY DOMAINS
The curriculum encompasses fundamental and advanced topics, from ethical hacking to compliance and risk management, making it an end-to-end program.
GLOBAL STANDARDS AND RELEVANCE
The course is aligned with ISO 27001 standards, OWASP Top 10, and other globally recognized frameworks, ensuring learners gain industry-relevant knowledge.
CAREER GROWTH OPPORTUNITIES
Cybersecurity certifications like CNSEHS can significantly enhance your career prospects, with roles like Security Analyst, Ethical Hacker, and Cybersecurity Consultant in high demand.
Program Advantages
Industry-packed courses: designed to align with the latest industry requirements, covering topics such as web app protection, network vAPT, cryptography and risk management.
Hands-On Learning: Practical sessions help to develop practical skills using devices such as NMAP, Burp Suite, Metasploit and Owasp juice shops.
Expert Guidance: Learn from experienced trainers who bring the actual world insight into cyber security challenges and solutions.
Global Certification: The program provides a valuable credit that validates your expertise in cyber security and moral hacking.
Career Flexibility: Different roles such as penetration testers, network safety experts and information security manager.
Study of the case of the real world: analyze and simulate attacks to understand weaknesses and mitigation strategies.

Certified Network Security and Ethical Hacking Specialist program Certifications
Nasscom

Course Completion

Project Completion
Certified Network Security and Ethical Hacking Specialist Curriculum
Certified Network Security and Ethical Hacking Specialist Skills Covered
Certified Network Security and Ethical Hacking Specialist Tools Covered













Certified Network Security and Ethical Hacking Specialist Program Benefits

CAREER OPPORTUNITIES AFTER THIS COURSE
Cybersecurity Analyst Salary Range
Min
$90,000
Average
$108,000
Max
$112,399

Projects that you will Work On
Practice Essential Tools
Designed By Industry Experts
Get Real-world Experience
Capstone Projects of this Program
Job Obligation After This Course
WE CAN APPLY FOR JOBS IN
Conduct security assessments and penetration tests.
Identify and mitigate vulnerabilities in systems and networks.
Monitor and respond to security incidents.
Implement and manage cybersecurity policies and frameworks.
Ensure compliance with security standards such as ISO 27001, GDPR, and NIST.
Perform risk analysis and develop mitigation strategies.
Companies Hiring for this Course
















































































































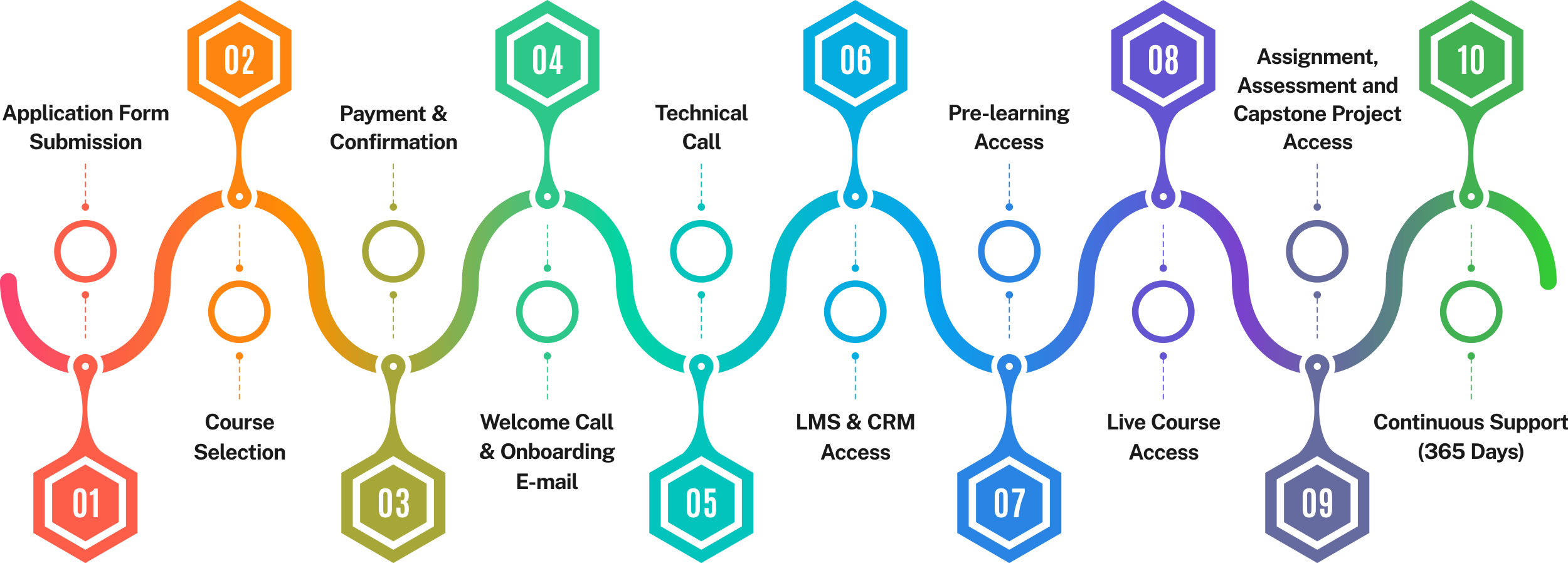
Admission Process
The application process consists of three simple steps. An offer of admission will be made to selected candidates based on the feedback from the interview panel. The selected candidates will be notified over email and phone, and they can block their seats through the payment of the admission fee.
Course Fees & Financing
We partnered with financing companies to provide competitive finance options at 0% interest rate with no hidden costs.


UPCOMING BATCHES/PROGRAM COHORTS
| Batch | Date | Time (IST) | Batch Type |
|---|---|---|---|
| Online Live Instructor Led Session | 23 November 2025 | 9 PM to 12 AM | Batch 1 |
| Online Live Instructor Led Session | 30 November 2025 | 9 PM to 12 AM | Batch 2 |
COMPARISON WITH OTHERS
| Feature | Our Course | COMPETITOR A | COMPETITOR B | COMPETITOR C |
|---|---|---|---|---|
| Program Duration | 8 months (550 Hours) | 5 Days (40 Hours) | Self-paced (90+ Days) | 5 Days |
| Total Learning Hours | 550 Hours | 40 Hours | 100+ Hours | 50+ Hours |
| Live Sessions | 180 Hours | 40 Hours | No Live Sessions | 40+ Hours |
| Self-Paced Learning | 50 Hours | Optional Add-ons | Fully Self-Paced | Yes |
| Pre-Learning Material | 50 Hours | No | Yes | Yes |
| Faculty | Industry Experts | CEH Certified Trainers | OSCP Certified Experts | SANS Instructors |
| Practical Learning | 40+ Projects & Case Studies | Labs & Exam Challenges | Hands-on Lab Exam | Labs & Practical Challenges |
| Mentorship & Career Support | 1:1 Mentorship, Mock Interviews, Placement Assistance | No Placement Assistance | No Career Support | No Placement Assistance |
| Certification | SkillzRevo CNSEHS Certificate | EC-Council CEH Certified | OSCP Certified | GPEN Certified |
| Industry Standards & Compliance | ISO 27001, GDPR, OWASP Top 10, NIST | ISO 27001, NIST, OWASP Top 10 | OSCP Ethical Hacking | GIAC Security Essentials |
| Key Topics Covered | Ethical Hacking, Web Security, Network Security, Risk & Compliance, Cryptography | Ethical Hacking, Penetration Testing, Social Engineering | Advanced Penetration Testing, Exploitation Techniques | Advanced Network Penetration Testing, Exploit Development |
| Tools Used | Nmap, Burp Suite, Metasploit, OWASP Juice Shop, DVWA, Wireshark, Hydra, OpenSSL | Metasploit, Nessus, Burp Suite | Kali Linux, Metasploit, ExploitDB | Nessus, Metasploit, Scapy |
| Hands-On Labs | Yes (Dedicated Lab Environments) | Yes (iLabs Add-on) | Yes (Proving Grounds) | Yes |
| Exam Format | Hands-on Projects & Case Studies | MCQ-based + Practical | 24-Hour Practical Exam | Practical Assessment |
| Job Placement Support | Yes (Dedicated Team) | No | No | No |
| Career Roles | Ethical Hacker, Cybersecurity Analyst, Penetration Tester, Risk & Compliance Analyst | Ethical Hacker, SOC Analyst | Penetration Tester, Red Team Specialist | Security Consultant, Penetration Tester |
| Salary Expectation | $6,000 - $50,000+ annually | $8,000 - $45,000 annually | $10,000 - $60,000+ annually | $12,000 - $70,000+ annually |
| Hiring Companies | Wipro, TCS, Infosys, HCL, Accenture, IBM, Deloitte, KPMG, PwC | Accenture, IBM, Infosys, EY | Red Team & Security Firms | Fortune 500 Companies, Government Agencies |
| Eligibility Criteria | Students, IT Professionals, System Administrators, Developers | IT Professionals, Security Analysts | Advanced Cybersecurity Professionals | Mid to Senior-Level Cybersecurity Professionals |
| Prerequisites | Basic IT & Networking Knowledge | Basic IT & Networking Knowledge | Strong IT & Linux Knowledge | Basic to Intermediate IT Security Knowledge |
| Cost | Affordable & No-Cost EMI | $$$ (High Cost) | $$$ (Expensive) | $$$$ (Very Expensive) |
| Admission Process | Easy Enrollment, Application, Payment, Onboarding | Exam Voucher Purchase & Training | Direct Registration & Self-Study | Training + Exam Bundle Purchase |