Cyber Security
Beginner to Mastery
Certified Security Operations & Incident Specialist
Weekly sessions with industry professionals
250 hours of structured learning experience
30 hours of pre-learning material for foundational understanding
70 hours of live training with expert instructors

Course Duration
250 Hours
Next Batch
23 November 2025
Course Material
Live. Online. Interactive.
70 hours of recorded video lectures for flexible learning
5 hours of capstone project discussion and doubt-clearing sessions
75 hours of hands-on involvement in capstone projects
3-hour duration for each live lecture

KEY HIGHLIGHTS OF CERTIFIED SECURITY OPERATIONS & INCIDENT SPECIALIST PROGRAM
- Comprehensive Cybersecurity Training: Covers security operations, incident handling, ethical hacking, SIEM (Splunk), forensic analysis, and system hardening.
- Hands-On Practical Approach: Includes real-world use cases, simulated cyber breach exercises, and practical implementation of security tools.
- Industry-Standard Tools: Training on Splunk, Nessus, Cisco IOS Firewall, VPNs, and forensic tools like Autopsy & FTK Imager.
- Incident Response & Forensics: Teaches security incident detection, analysis, and forensic investigation techniques.
- SOC Operations: Covers Security Operations Center (SOC) architecture, roles, and responsibilities.
- Threat Intelligence & Attack Analysis: Provides knowledge on MITRE ATT&CK framework, Indicators of Compromise (IOCs), and Indicators of Attack (IOAs).
- System Hardening & Auditing: Focus on security configuration, audits, vulnerability scanning, and patch management.
- 24 instructor-led live lectures spread over 12 weeks
- 11 industry-relevant modules covering key concepts
- 10 assignments and 5 assessments to evaluate learning
- 10+ real-world capstone projects for practical exposure
- Designed for both working professionals and fresh graduates
- High-demand career opportunities with industry recognition
- Flexible learning with access to recorded sessions
- 24/7 support and a dedicated learning management team
WHY JOIN CERTIFIED SECURITY OPERATIONS & INCIDENT SPECIALIST PROGRAM?
Hands-On Learning
Gain practical experience with tools like Splunk, Nessus, and FTK Imager.
Industry-Relevant Skills
Stay competitive with up-to-date cybersecurity expertise.
Expert Training
Learn from seasoned professionals with real-world insights.
High Demand
Cybersecurity professionals are in urgent demand, boosting career prospects.
UPCOMING BATCH:
23 November 2025

SkillzRevo Solutions
30 MINUTE MEETING
Web conferencing details provided upon confirmation.
Corporate Training, Enterprise training for teams
Batch schedule
| Batch | Batch Type |
|---|---|
| Online Live Instructor Led Session | Full-Time |
| Online Live Instructor Led Session | Part-Time |
Regional Timings
| Batch | Batch Type |
|---|---|
| IST (India Standard Time) | 09:00 PM–12:00 AM |
| Bahrain, Qatar, Kuwait, Saudi Arabia | 06:30 PM–09:30 PM |
| UAE / Oman | 07:30 PM–09:00 PM |
Certified Security Operations & Incident Specialist OVERVIEW
The Certified Security Operations and Incident Handling Specialist (CSOIS) program provides intensive knowledge and expertise on cyber safety operations, events and forensic examinations. Participants will learn the incident, firewall configuration, infiltration detection and patch management. The program includes SOC architecture, IOCs, IOAs, TTPs using the MITRE ATT&CK, and experience on hands with SIEM tools such as splunk. Students will gain proficiency in strict, vulnerable scanning and cyber forensic, including students memory and disc analysis. Through the study of the real -world case and practical laboratories, this program equips professionals with the skills required for SOC operations, event reaction and digital forensic roles in cyber security.
ENROLL NOW & BOOK YOUR SEAT AT FLAT 50% WAIVER ON FEE
Enroll Now →Certified Security Operations & Incident Specialist Objectives
The CSOIS program equips participants with skills in security operations, incident handling, and threat intelligence. It covers SOC operations, firewall management, IDS/IPS, SIEM tools like Splunk, and vulnerability management using Nessus. Learners will gain hands-on experience in cyber forensics, memory and disk analysis, and forensic investigations. The course includes real-world case studies and practical exercises to ensure effective incident response and cybersecurity threat mitigation.
Enroll Now →Why Learn Certified Security Operations & Incident Specialist ?
Comprehensive Curriculum
Covers incident response, SIEM, forensics, and vulnerability management.
Real-World Simulations
Train with case studies and security breach scenarios.
Cyber Forensics Specialization
Develop expertise in rootkit detection and digital investigations.
Real-World Application
Certification
Growing Industry
Cybersecurity offers long-term stability and career advancement.
Cutting-Edge Tools
Work with advanced security platforms used by top organizations.
SOC Operations Mastery
Learn tools and processes to manage Security Operations Centers.
MITRE ATTACK & Threat Intelligence
Learn advanced techniques to detect and reduce security hazards.
Program Advantages
Extensive coverage: The event covers incident handling, security options, network attacks and systems strict.
Hands-on Exposure: Work with Splunk, Nesses, FTK Imager, Firewall Setup and Log Analysis.
Safety understanding: SOC roles, Threat Intelligence and SOC learning architecture.
Forensics and Investigation: Cyber forensic, specialize in detection and safety analysis of rootkit.
Frameworks and TTPs: Master MITRE ATT&CK, IOCs and Attack Lifestyle Management.
Career Advancement: Industry Certificate for SOC and IR roles and training on hands.
Security Configuration: Learn Firewall, IDS/IPS tuning and router security.

Certified Security Operations & Incident Specialist program Certifications
Nasscom

Course Completion

Project Completion
Certified Security Operations & Incident Specialist Curriculum
Certified Security Operations & Incident Specialist Skills Covered
Certified Security Operations & Incident Specialist Tools Covered






Certified Security Operations & Incident Specialist Program Benefits

CAREER OPPORTUNITIES AFTER THIS COURSE
Cyber Forensic Analyst Salary Range
Min
$80,000
Average
$92,000
Max
$180,000

Projects that you will Work On
Practice Essential Tools
Designed By Industry Experts
Get Real-world Experience
Capstone Projects of this Program
Job Obligation After This Course
WE CAN APPLY FOR JOBS IN
Conduct security assessments and penetration tests.
Identify and mitigate vulnerabilities in systems and networks.
Monitor and respond to security incidents.
Implement and manage cybersecurity policies and frameworks.
Ensure compliance with security standards such as ISO 27001, GDPR, and NIST.
Perform risk analysis and develop mitigation strategies.
Companies Hiring for this Course
















































































































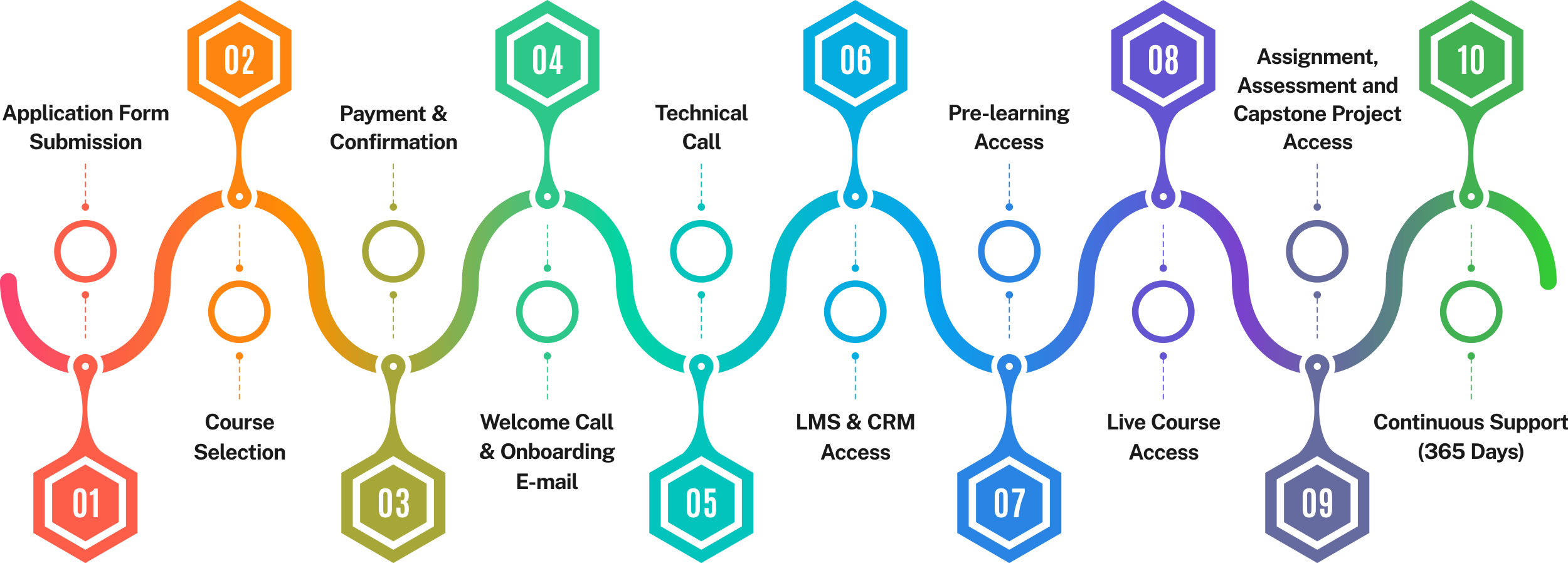
Admission Process
The application process consists of three simple steps. An offer of admission will be made to selected candidates based on the feedback from the interview panel. The selected candidates will be notified over email and phone, and they can block their seats through the payment of the admission fee.
Course Fees & Financing
We partnered with financing companies to provide competitive finance options at 0% interest rate with no hidden costs.


UPCOMING BATCHES/PROGRAM COHORTS
| Batch | Date | Time (IST) | Batch Type |
|---|---|---|---|
| Online Live Instructor Led Session | 23 November 2025 | 9 PM to 12 AM | Batch 1 |
| Online Live Instructor Led Session | 30 November 2025 | 9 PM to 12 AM | Batch 2 |
COMPARISON WITH OTHERS
| Feature | Our Course | COMPETITOR A |
|---|---|---|
| Comprehensive Curriculum | Covers Security Operations, Incident Handling, SIEM, Forensics, and more | Often focuses on only one or two aspects of security |
| Real-World Tools & Practical | Hands-on training with tools like Splunk, Nessus, Rkhunter, FTK Imager | Limited or no hands-on exposure to real-world tools |
| Incident Response Lifecycle | In-depth coverage of the full incident response lifecycle from detection to recovery | Basic coverage, lacks detailed incident handling stages |
| Cyber Forensics | Includes digital forensics, rootkit detection, and evidence handling | Minimal to no focus on forensics |
| Expert Trainers | Led by industry experts with years of practical experience | Trainers may have limited industry experience |
| Post-Course Support | Ongoing support and mentorship for career development | Limited or no post-course support |
| Industry Recognition | Recognized by top cybersecurity organizations and employers | May lack industry certification or recognition |
| Tailored for Career Growth | Focused on career progression with skills that directly align with current job market needs | Generic content that may not align with specific career goals |
| Interactive Learning | Interactive lessons with real-life scenarios, case studies, and practical exercises | Passive learning, often relying on lectures or theory |